Review: APISEC - API Penetration Testing Course
I recently acquired “Hacking APIs” by Corey Ball (https://nostarch.com/hacking-apis), as there has been an increasing demand for API-specific testing. I will say that the book exceeded my expectations, and I can confidently recommend it to anyone in the field. At the very least, it serves as excellent reference material, even if you are already quite familiar with APIs.
I mention the book, really as a way to make a comparison. At some point, while reading the book I was made aware of a free security course where the instructor was none other than Corey Ball himself. It seems that with the release of the book he also founded APISEC Univerisity (https://www.apisecuniversity.com/) with an obvious focus on API security training. At the time of writing this, the only course available is “API Penetration Testing” although it does appear there are a few other fundamental courses on the way.
Having completed the “API Penetration Testing” course I am left a little at odds with how I feel about its quality.
A large part of this review focuses on the negative experiences I had with the course at the time I took it, with any luck those items will be addressed, I do not want to completely dissuade anyone from looking into this free resource.
For some reference before I start to go into details, the course is delivered in sections and does not assume you have the “Hacking APIs” book. Most sections start with a practical, follow-along, type of instructional video where tasks are performed against the “completely ridiculous API (crAPI)” offered by OWASP (https://github.com/OWASP/crAPI). Following these videos is usually a type of comprehension quiz where they ask you questions that are covered by the video directly, although this is not always the case. Once you reach the API-specific security topics an end-of-section assessment is also included where you practice the techniques covered on a different application, “Vulnerable Adversely Programmed Interface (vAPI)” (https://github.com/roottusk/vapi), which is not shown in the video content. For each section, you must score a 100% on both the quiz and assessment before you can move on, although this means very little as I will explain in a moment.
The bad and the ugly
Let’s start with the bad and the ugly. If you decide to give the course a try, and I’m not saying you should avoid it, there are a few things you should know going in. Whoever put the end-of-section assessments together must have been rushed or just not cared to do any checking/testing. There were several instances where provable answers against the vAPI application were not reflected correctly in the assessment and at least one instance of a flat-out incorrect answer.
For example one of the early quiz modules asked the question "When using a command line tool like JWT_tool what commands/options can be used to learn how to use it?" and you were asked to select all answers that apply. The issue is that the answers expected seem to be a matter of opinion on what parts of the application teach you how to use it, and just an incorrect assumption. For this instance, almost every answer is valid for the question even though the correct answers include things like $jwt_tool which would just output the usage flags and not the help context which I guess can be argued is technically correct but it seems silly to count this when actual useful information is only a -h away. Another correct answer of $man jwt_tool is also included in the quiz which if set up the way you are instructed to produces the response No manual entry for jwt_tool. And this is not the only instance, there are a few questions over the several quizzes and assessments that with just some simple rephrasing could go a long way to expecting and providing a more concise answer.
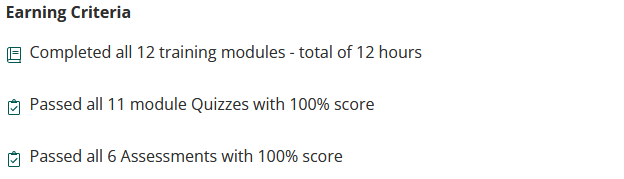
The most egregious of these quiz/assessment issues comes near the end of the course in the “API Injection Assessment”. There is a big issue with this assessment which also highlights a strange design decision. First the issue, at the time of writing this at least one of the questions asking about response codes expects a flat-out wrong answer, and the question asking "Which payload results in a successful injection attack on vAPI?" asks you to select a single correct answer out of a list of 12 possible answers, of which half of the MySQL-focused answers will provide you with a successful injection and the one the tests expected is one of the few that were rejected. Back to me mentioning that the 100% clearing score was essentially meaningless. When you take a section quiz all of the questions are on one page you submit when you are done selecting your answers, if you happen to get a wrong answer the platform will show you the correct answers and you can simply review the mistake you made, quickly retake the quiz, and move one. If you make a mistake on an assessment you will receive a failed notice but the platform does not show you where the mistake is, at least not on the course page the way it does for a quiz. Additionally, the assessment is presented one question at a time that you click through. This led to me angrily re-taking the assessment test for this section several times with verifiable correct answers and getting more and more irritated every time I reached the end of the assessment and it provided me with a “failed” prompt. After doing this several times I noticed that every time I failed the assessment I was getting an email, and this email contained a breakdown of all the expected “correct” answers. This allowed me to swap the two answers I had verified as correct for the expected answers that I could verify as incorrect and pass the exam. But if you are going to provide the answers to the assessment anyway why not provide them on the platform the same way they are provided for the quiz, it did not make sense to me. It also made it apparent that the 100% clear rate was more of a marketing gimmick, even the Credly badge and certificate of completion you obtain when you finish the course go out of their way to mention that passing all quizzes and assessments with a 100% score is part of the earning criteria.
The ‘Earning Criteria’ as listed on Credly
With any luck the assessments and quizzes will be updated, I made the issues known in the APISec discord server and after a quick search, it was clear I was not the only one who noticed these problems.
The good
Now a bit about the good. I know I just got done hitting you with a wall of text covering what should have been minor frustrations. But for starters it’s free, and it is hard not to recommend a free resource that contains useful information with so many people trying to break into the field on a budget. I feel that if I could have gone in knowing the existing issues mentioned above I would have enjoyed the course much more than I did.
Although in my opinion not as polished and digestible, the course does cover many of the same topics from the “Hacking APIs” book with many of the sections being a 1-to-1 translation to a follow-along video format. So you can get a lot of the same information from the book through this free course.
There is also a fairly active Discord server for APISec presented to you in the course, and the people there are friendly enough to let you know you are not going crazy when you run into one of the previously mentioned issues.
Reccomendations
If you can afford it, definitely buy the “Hacking APIs” book, it’s a solid book and I can only imagine it will serve me well as reference material. I think the information is presented better in this format, maybe that is thanks to having a technical reviewer, and it will have a spot on the security bookshelf for a long time.
If you want some of the info with none of the cost, check out the training. Just keep in mind there are potentially some bits and pieces that don’t fit so nicely together, assuming they don’t get fixed, and you should be fine.
I will also say that in a world where your skills are typically being judged by non-technical people such as human resources or staffing teams, having something as simple as a certificate of completion in a specific subject can go a long way to getting you in front of the people who do know the technical stuff. So if you have a free weekend to power through it, you might as well grab the badge and certificate of completion for your LinkedIn profile.
The ‘API Penetration Testing’ Badge on Credly